
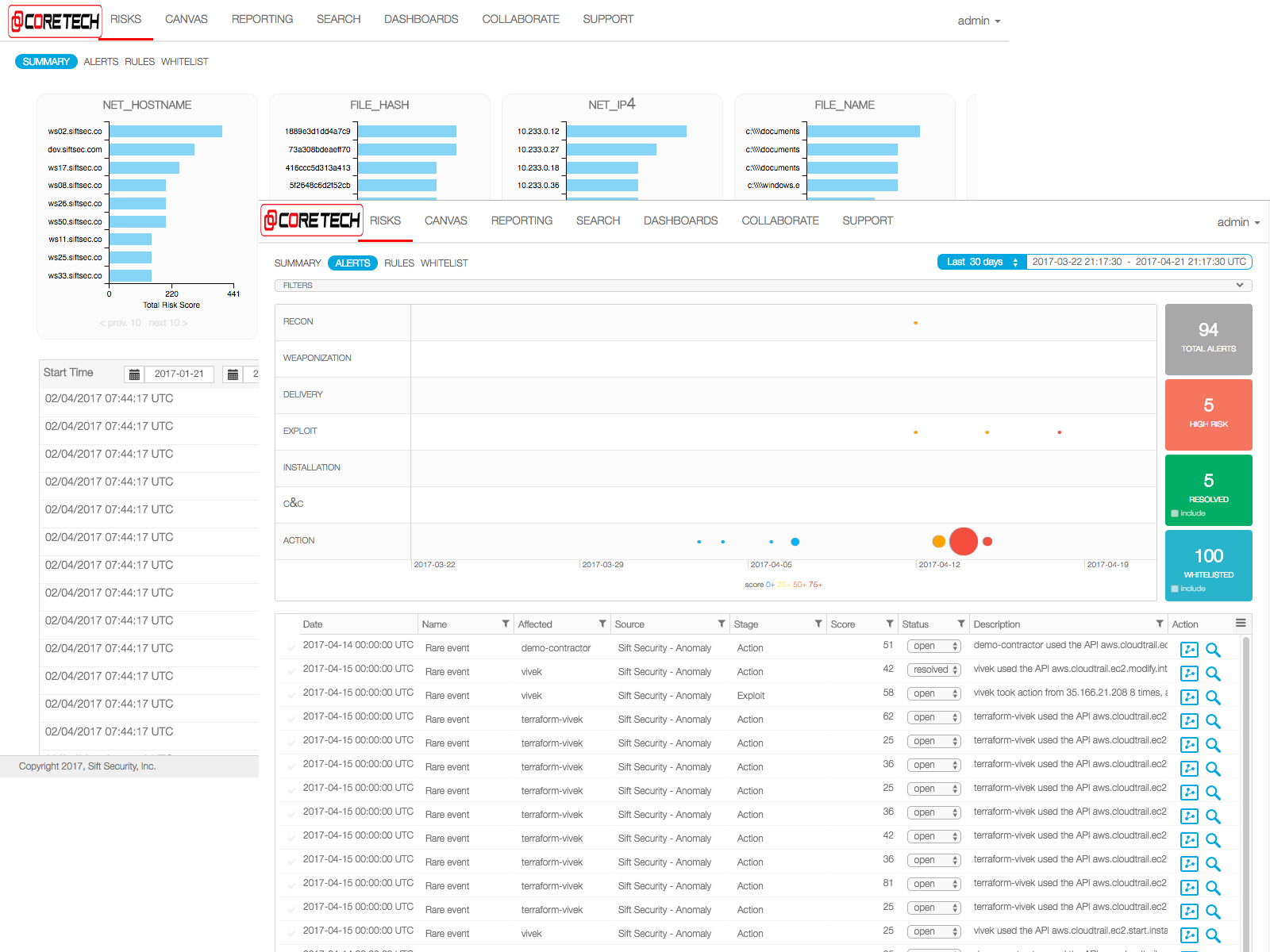
Analysts can quickly review and respond to prioritized alerts from 3rd parties, rules, and CoreTech Security machine learning, all mapped to the kill chain.
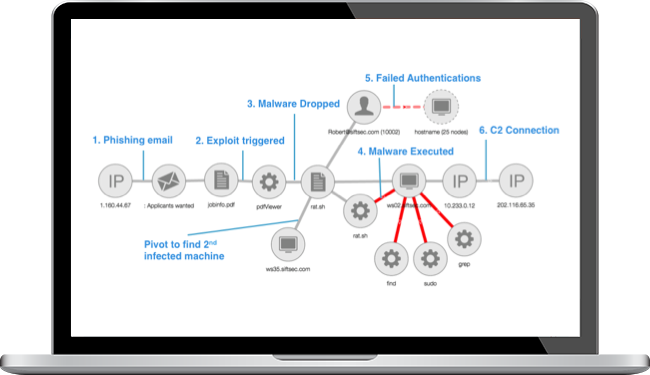
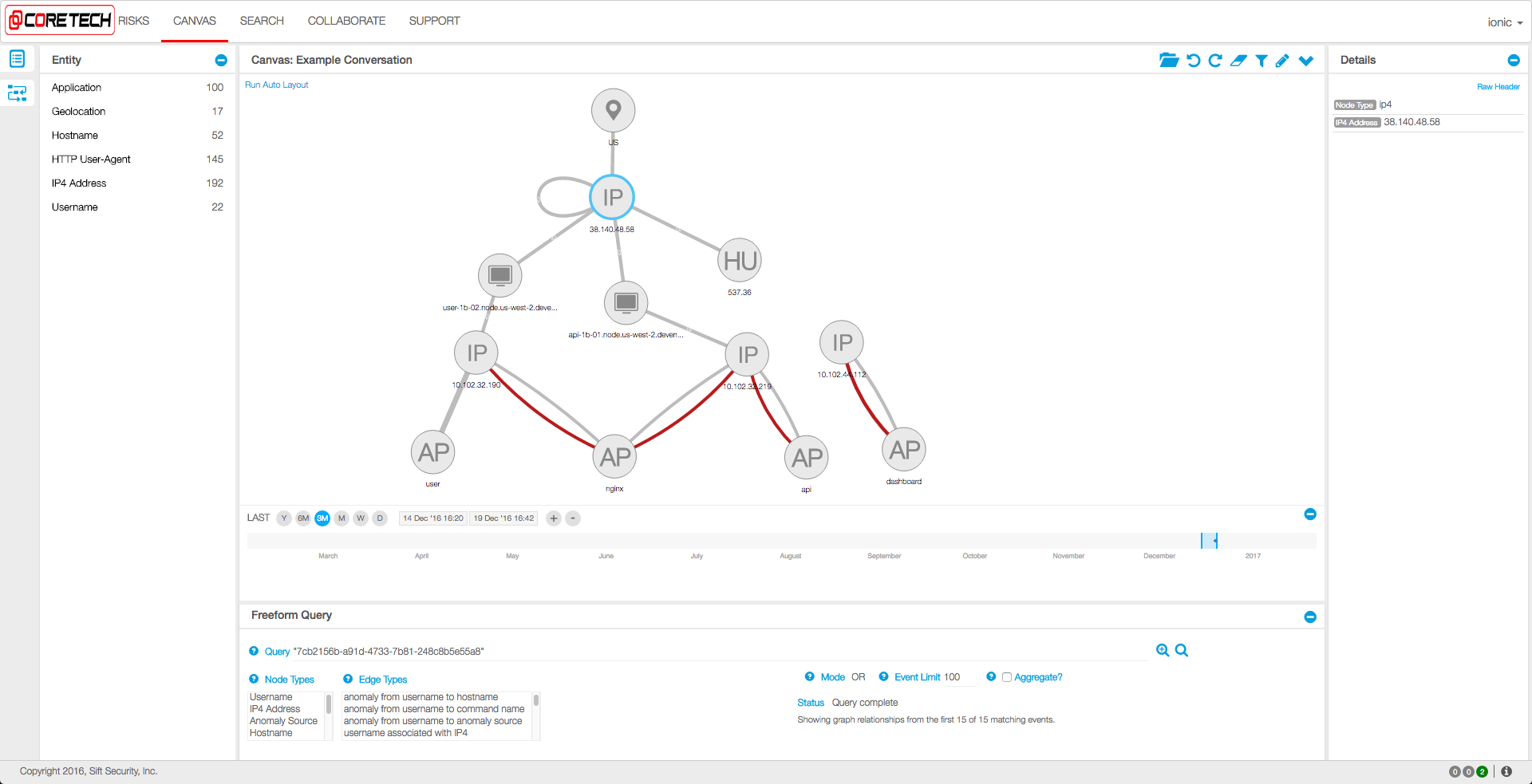
Hunters get high quality starting points, provided by CoreTech Security's proprietary graph clustering algorithms which identify potential attack chains.
Responders can rapidly investigate events and seamlessly take action to stop attacks.
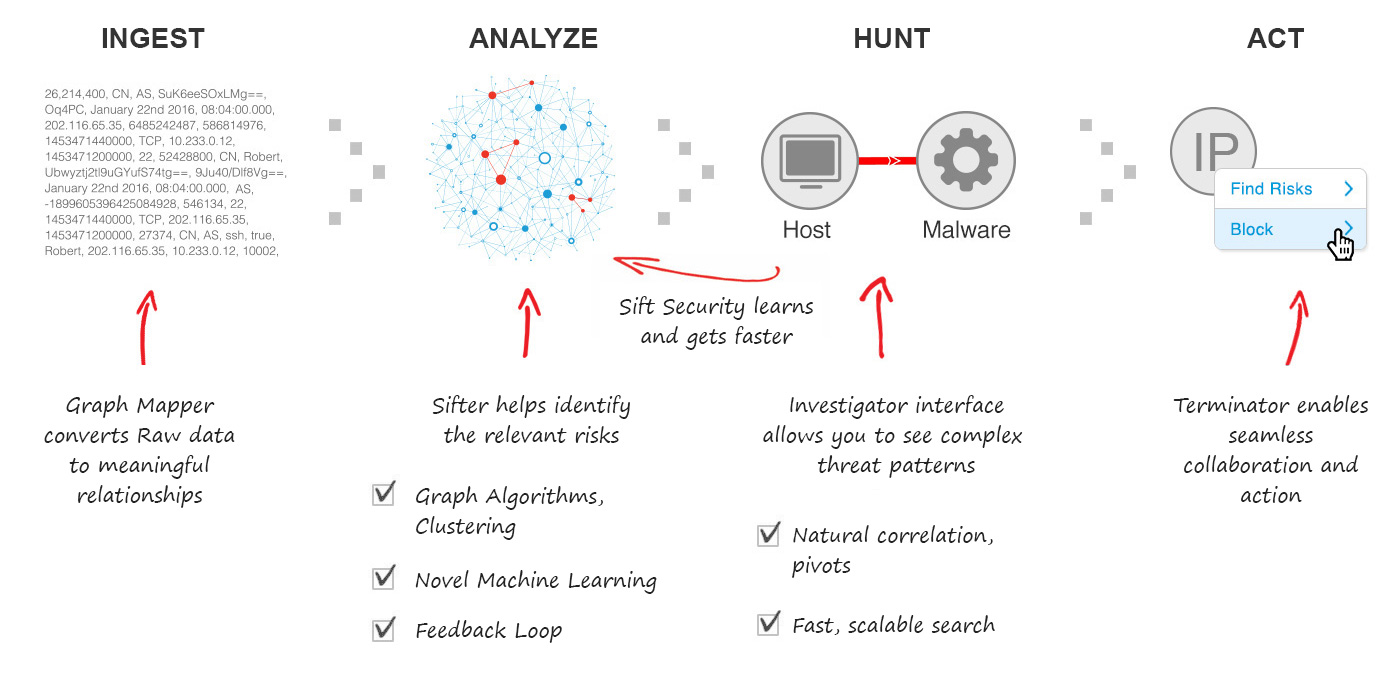
Scalable graph-centric data analytics platform
It is easy to dump large volumes of data in Hadoop or an index, but getting value out of the data can be challenging. Graph databases offer many advantages, but can be difficult to scale. CoreTech Security take away the complexity and maps data into a graph data structure in a way that applies security context, enables workflow, and supports massive scale.
Machine learning and graph algorithms
It is easy to develop lots of narrow, rigid detection use cases, but security teams don’t have time to set up and maintain these rules. CoreTech Security is productizing machine learning in a way that allows users to easily apply algorithms that effectively address security use cases and work at large scale.
Advanced visualization, automation & orchestration
It is easy to make pretty graphs with simple data, but it is hard to create intuitive workflow, automation, and collaboration that truly simplifies and speeds up security operations and incident response. CoreTech Security was built from scratch with a graph first approach to investigations and offers simple and effective visualization and workflow.

Al Quoz Industrial area 3, Behind Traffic Department, Near Mall of Emirates, Dubai, UNITED ARAB EMIRATES
Phone : +971 4 314 7500
contact@coretech.ae