Use Cases
CoreTech Security's scalable graph analytics platform enables many security use cases to enable organizations to get more out of their security and cloud operations, incident response, and threat hunting teams.
CoreTech Security can be deployed standalone or integrated with your existing SIEM platform.
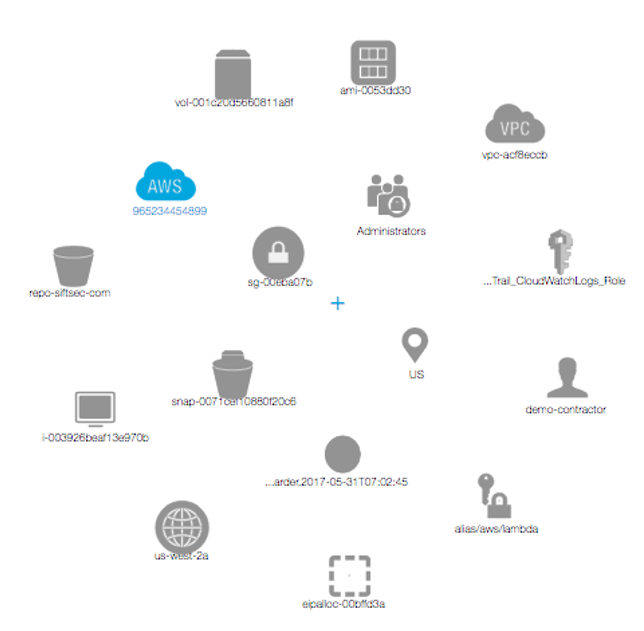
With CoreTech Security, you can more easily stay in compliance with best practices, as well as quickly detect and respond to risks. CoreTech Security uniquely leverages graph analytics & machine learning to supercharge your operations teams. CoreTech Security offer protection across multiple dimensions: Network Security, IAM Protection, and Compliance.
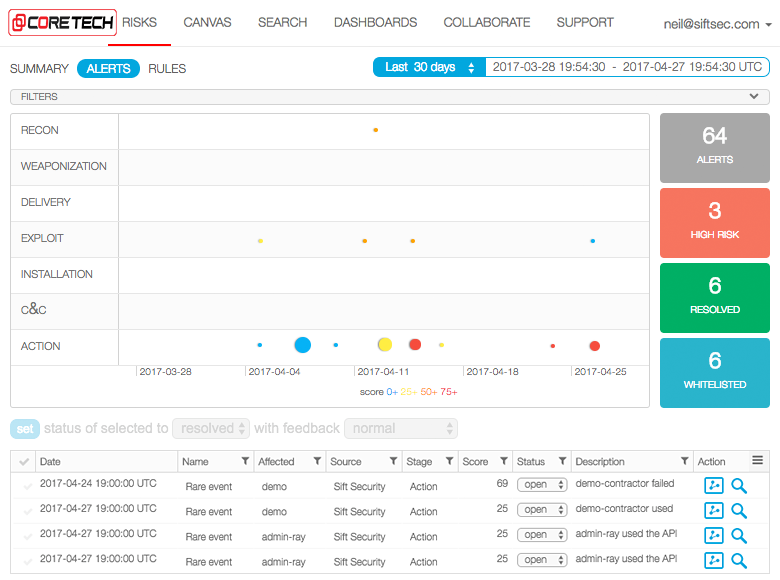
Security teams at many organizations generate more alerts than they can effectively handle. Their firewalls are too chatty. Their antivirus solution generates the same alerts all the time. Their threat intel feeds generate too many false positives. Going through them and manually whitelisting things is too much work – a system that automatically identifies the important alerts is desired.
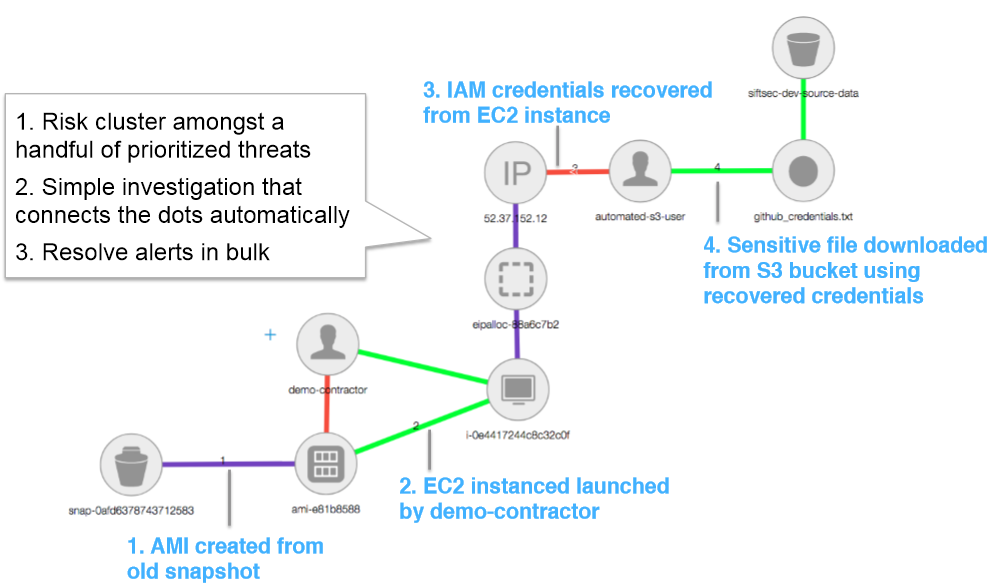
Investigating a security incident can involve wrangling dozens of data sources. To uncover a successful phishing attack, you might have to integrate email records, process executions, user behavior, file access, netflow, antivirus alerts, etc. Gathering and correlating those logs is slow and cumbersome, making it difficult to follow the attack chain. CoreTech Security's product extracts the most important information from disparate data sources into one straightforward, scalable system: a relational graph. Using the graph makes investigations faster, easier, and more intuitive.
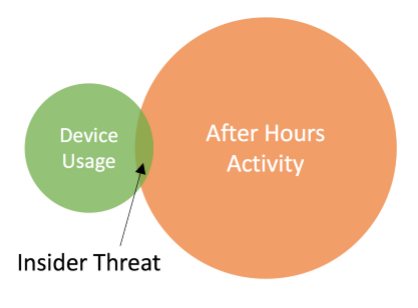
Many large enterprises are moving towards automation of repetitive tasks typically associate with alert triage. As a result, more resources will become available to proactively hunt for threats. Threat Hunting is a highly specialized and typically inefficient process, leaving many organizations struggling to find enough talent to perform this task effectively.
CoreTech Security can help.

Al Quoz Industrial area 3, Behind Traffic Department, Near Mall of Emirates, Dubai, UNITED ARAB EMIRATES
Phone : +971 4 314 7500
contact@coretech.ae